
 Security Acceleration cdn
Security Acceleration cdn
 High protection against IP forwarding
High protection against IP forwarding
 WEB application firewall
WEB application firewall
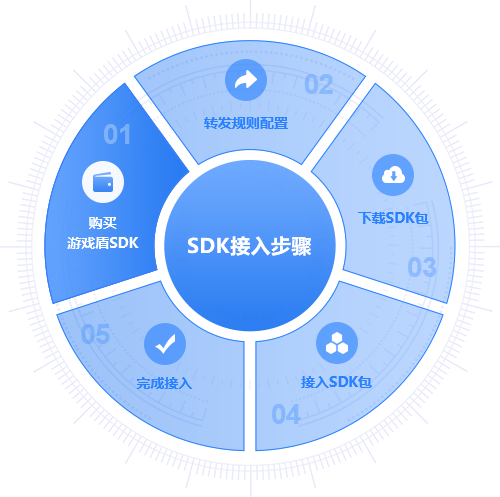
 Game SDK Shield
Game SDK Shield
Web security acceleration
Provide various types of attack protection such as DDOS, CC, page tampering, crawling, etc. for website businesses such as gaming, e-commerce, finance, healthcare, portal, etc
IP forwarding
Support DDoS and CC protection for website and non website businesses. Users can configure forwarding rules to redirect attack traffic to the SPDN advanced defense IP for traffic cleaning
web application firewall
Sudun Web Application Firewall WAF automatically protects against web vulnerabilities, conducts multi-dimensional detection and security protection of website business traffic, and avoids hacker and virus intrusion
Game SDK Shield
Provide SDK downloads containing Windows, Android, and IOS versions. By connecting to the SDK, the SDK takes over all communication traffic for scheduling and encrypted transmission




 Unlimited DDoS attack protection
Unlimited DDoS attack protection

